Figure 0 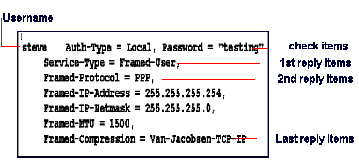
RADIUS Accounting Server. If you implement RADIUS accounting, you must also select one or more RADIUS accounting servers. The RADIUS accounting server can be located on the same host as the RADIUS server used for authentication, or on a separate host.
Secondary RADIUS Accounting Server. You can define a secondary accounting server to serve as a backup if the primary server cannot be contacted. For example, PortMaster always sends accounting packets to the primary RADIUS accounting server first, and retries it once every 45 seconds. If the primary server does not respond within 10 minutes, or if more than 50 accounting packets are waiting to be sent, the PortMaster sends the accounting packets to the secondary RADIUS accounting server.
1. Modify the clients file to add the NAS and shared secret.
2. Configure the following on the NAS and save the configuration changes.
- Security enabled on all ports
- IP addresses of the primary and optional alternate RADIUS authentication servers; optionally configure an authentication port number different from the default
- IP addresses of the primary and optional alternate RADIUS accounting servers, if accounting is to be performed; optionally configure an accounting port number different from the default
- RADIUS shared secret
The clients file contains the shared secrets for the RADIUS clients, and this information must be protected from unauthorized access.
The permissions on a UNIX host look like this:
-rw------- 1 root daemon 802 Jul 15 00:21 clients
2. To add a client, enter the client's name or IP address and the shared secret. To add a comment line, start the line with the number sign (#).
Shared secrets must consist of 15 or fewer printable, nonspace, ASCII characters. There is no limit to the number of clients that you can add to this file.
Here are some examples of client names and shared secrets:
#Client Name Shared Secret
#------------------------------
t1.dialup.afnog.org wP40cQ0
t2.dialup.afnog.org A3X445A
192.168.1.2 wer369st
Use IP addresses to avoid the DNS lookup time entailed by using client names and possible incorrect name translation.
Client configuration lines on a cisco 2511 (t1.dialup.afnog.org)
aaa new-model
radius-server host 192.0.2.1
radius-server key wP40cQ0
Figure 0 
2. password check item
3. other check items
You must place DEFAULT profiles at the end of the users file. RADIUS stops scanning profiles when a matching DEFAULT profile is found and ignores any user profiles located after a DEFAULT user profile.
Service-Type = Framed-User,
Framed-Routing = None,
Framed-Protocol = PPP,
Framed-IP-Address = 255.255.255.254,
Framed-MTU = 1500
DEFAULT1 Auth-Type = System, Called-Station-Id = 9255551234
(reply items)
DEFAULT2 Auth-Type = System, Called-Station-Id = 9255554971
(reply items)
| Item | Options | Explanation |
|---|---|---|
| Auth-Type | Local | User's password is stored in the RADIUS users file. Default. |
| System | User's password is stored in a system password file. | |
| ActivCard | User is authenticated via ActivEngine software | |
| SecurID | User is authenticated via ACE/Server software. | |
| Reject | User always fails authentication. | |
| Called-Station-Id | String of numerals | Telephone number called by user. |
| Calling-Station-Id | String of numerals | Telephone number user is calling from. |
| Connect-Rate | String of numerals | Maximum connection rate permitted, in bps. |
| Crypt-Password | User's password | User's password is stored in UNIX crypt format. CHAP authentication attempts fail if Crypt-Password is used, even if the password is correct. |
| Expiration | Must be specified in "Mmm dd yyyy" format | Date that user's password expires. |
| Framed-Protocol | PPP | PPP is used for the connection. Can also be used as a reply item. |
| Group | String of characters in double quotation marks (" ") | Groups that user belongs to. |
| NAS-IP-Address | IP address | NAS IP address. |
| NAS-Port | Number | The NAS port number that the user is dialed in to (for example, NAS-Port = S2). |
| NAS-Port-Type | ISDN | ISDN port. |
| Async | Asynchronous port. | |
| Sync | Synchronous port. | |
| ISDN-V120 | ISDN in V.120 mode. | |
| ISDN-V110 | ISDN in V.110 mode. | |
| Password | String of characters in double quotation marks (" ") | User's password. |
| Prefix | String of characters in double quotation marks (" ") | Removed from beginning of username before checking password. |
| Service-Type | Call-Check | Authenticates the user at the point of entry on a NAS before answering the call. The NAS must support an ISDN Primary Rate Interface (PRI). You must also configure the call-check feature on the NAS. |
| Framed-User | User uses PPP or SLIP for the connection. Can also be used as a reply item. | |
| Outbound-User | User makes outbound connections via Telnet. Can also be used as a reply item. | |
| Suffix | String of characters in double quotation marks (" ") | Removed from end of username before checking password |
| Item | Options | Explanation |
|---|---|---|
| Callback-Id | Location name in double quotation marks (" ") | Specify only for Service-Type = Callback-Framed-User. Location must be in NAS location table. |
| Callback-Number | Phone number in double quotation marks (" ") | Specify only for Service-Type = Callback-Login-User. |
| Filter-Id | Filter name | Filter name to be used for packet or access filtering on the interface. |
| Framed-Compression | None | If this reply item is omitted, Van Jacobson TCP/IP header compression is used. |
| Van-Jacobson-TCP-IP | Van Jacobson TCP/IP header compression is used for the connection. Default. | |
| Framed-IP-Address | IP Address | The user's IP address. |
| Framed-IP-Netmask | Netmask | The user's netmask. |
| Framed-IPX-Network | Dotted decimal IPX network number | IPX network number. |
| Framed-MTU | Number | Number of bytes in maximum transmission unit (MTU). |
| Framed-Protocol | PPP | PPP is used for the connection. Can also be used as a check item. |
| SLIP | SLIP is used for the connection. | |
| Framed-Route | Destination IP address | The IP address of the destination network. |
| Gateway IP address | The IP address of the gateway to the destination network. | |
| Metric | The number of routing hops to the destination network. Also known as the hop count. | |
| Framed-Routing | None | Disables RIP on the interface. |
| Broadcast | The interface sends RIP updates. | |
| Listen | The interface listens for RIP updates. | |
| Broadcast-Listen | The interface sends and listens for RIP updates. | |
| Idle-Timeout | In seconds | Specifies the idle time limit for a session. |
| Login-IP-Host | IP address | Address of the remote host. |
| Login-Service | Telnet | Establishes a Telnet connection to the remote host. |
| Rlogin | Establishes an rlogin connection to the remote host. | |
| TCP-Clear | Establishes a TCP clear connection to the remote host. | |
| PortMaster | Establishes a connection to the remote host using the PortMaster login service. | |
| Login-TCP-Port | TCP port number | TCP port number of the Login-Service. |
| Menu | Menu name in double quotation marks (" ") | Defines a menu in a user record. |
| Port-Limit | Number of B channels for ISDN Multilink PPP or Multilink V.120 | Specifies the maximum number of B channels a user can use. |
| Session-Timeout | In seconds | Specifies the time limit for a session. |
| Service-Type | Administrative-User | Grants user full access to all configuration commands. |
| Callback-Login-User | Calls user back and connects via Telnet, rlogin , PortMaster, or TCP-Clear login service. | |
| Callback-Framed-User | Calls user back and establishes a framed connection (PPP or SLIP). Location must be specified in NAS location table. | |
| Framed-User | User uses PPP or SLIP for the connection. Can also be used as a check item. | |
| Login-User | User connects via Telnet, rlogin , PortMaster, or TCP-Clear login service. | |
| NAS-Prompt-User | Grants user limited access to commands (nonconfiguration only). | |
| Outbound-User | User makes outbound connections via Telnet. Can also be used as a check item. | |
| Termination-Menu | Menu name in double quotation marks (" ") | Menu to display after service is terminated. |
2. Uses MD5 to encrypt the password, the CHAP ID octet, and the CHAP challenge.
3. Compares the result to the CHAP-Password.
4. If the items in Steps 2 and 3 match, the server sends an access-accept packet to the NAS. If there is no match, the server sends back an access-reject packet.
This is the default value.
2. Set passwords in clear text; they must not be encrypted.
3. Turn off PAP and turn on CHAP on the NAS.