- Port 1645 for authentication
- Port 1646 for accounting
How it works
This figure shows the interaction between a dial-in user and the RADIUS client
and server.
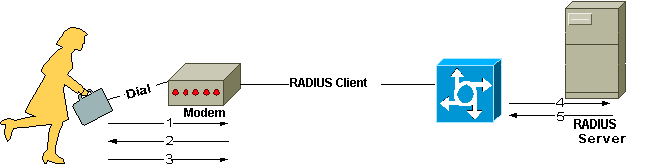
-
1- User initiates PPP authentication to the NAS.
- 2- NAS prompts for username and password (if PAP) or challenge (if CHAP).
- 3- User replies.
- 4- RADIUS client sends username and encrypted password to the RADIUS server.
- 5- RADIUS server responds with Accept, Reject, or Challenge.
- The RADIUS client acts upon services and services parameters bundled with Accept or Reject.
- RADIUS offers the following features:
Authentication and Authorization
When the RADIUS server receives the Access-Request from the NAS, it searches a database for the username listed. If the username does not exist in the database, either a default profile is loaded or the RADIUS server immediately sends an Access-Reject message. This Access-Reject message can be accompanied by a text message indicating the reason for the refusal.
In RADIUS, authentication and authorization are coupled together.
If the username is found and the password is correct, the RADIUS server returns
an Access-Accept response, including a list of attribute-value pairs that
describe the parameters to be used for this session. Typical parameters include
service type (shell or framed), protocol type, IP address to assign the user
(static or dynamic), access list to apply, or a static route to install in
the NAS routing table. The configuration information in the RADIUS server
defines what will be installed on the NAS. The figure below illustrates the
RADIUS authentication and authorization sequence.
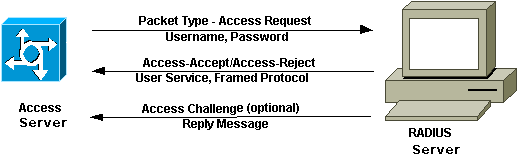
Accounting
Transactions between the client and RADIUS server are authenticated
through the use of a shared secret, which is never sent over the network.
In addition, user passwords are sent encrypted between the client and RADIUS
server to eliminate the possibility that someone snooping on an insecure network
could determine a user's password.
Features
In large networks, security information can be scattered throughout the network on different devices. RADIUS allows user information to be stored on one host, minimizing the risk of security loopholes. All authentication and access to network services is managed by the host functioning as the RADIUS server.
Flexibility
Using modifiable "stubs," RADIUS can be adapted to work with existing security
systems and protocols. You adapt the RADIUS server to your network, rather
than adjusting your network to work with RADIUS.
The RADIUS server stores security information in text files at a central location; you add new users to the database or modify existing user information by editing these text files.
RADIUS provides extensive accounting trail capabilities, referred to as RADIUS accounting . Information collected in a log file can be analyzed for security purposes or used for billing.
Enhancements
Proxy RADIUS
Proxy RADIUS enables your RADIUS server to forward authentication requests from a network access server (NAS) to a remote RADIUS server and to pass the reply back to the NAS. This feature enables cooperating Internet service providers (ISPs) to handle dial-in service requests from each other's users. Corporate users can easily forward packets from local to remote networks.
RADIUS now supports ActivCard authentication on the following platforms supported by ActivCard 2.1: AIX, HP-UX, Solaris, and Sun-OS. ActivCard authenticates users by means of dynamic passwords generated by a handheld token using the public Digital Encryption Standard (DES) algorithm. The RADIUS server can forward all requests specified by the user profiles to the ActivCard server.
Virtual ports
-
You can restrict the number of logins permitted to specified telephone
numbers.
-
The syslog message for many kinds of rejected access-requests
now includes the Calling-Station-Id--if known--enabling you to track down
where the failed login attempts are dialing from.
You can turn on RADIUS debugging by sending a SIGUSR1 signal to radiusd . Sending a SIGUSR2 signal to radiusd turns debugging off. The RADIUS server logs a short summary message of radiusd activity when either signal is sent and when radiusd is exited.
RADIUS Installation and Configuration
-
Table1 provides a quick overview of the tasks required to install and
configure RADIUS.
| Task |
|---|
| 1. Select a host to use as the RADIUS server. |
| 2. Install the RADIUS server software on the host. |
| 3. Configure client information on the RADIUS server. |
| 4. Configure the NAS as a RADIUS client. |
| 5. Configure user profiles. |
| 6. You can optionally define menus to enable authenticated users to select different login options. |
| 7. You can optionally install and configure RADIUS accounting. |
| 8. You can optionally configure RADIUS proxy service. |